With an increasingly large number of cyber-attacks rising from the past recent decade, DDoS attacks have been prevailing in all of these combining cyber-attacks. It is because it was easy for attackers to conduct DDoS attacks and affect millions of websites without much complexity.
Being a victim of DDoS attacks may feel like a side effect of having a website. The more successful and traffic your website gets, the higher chances of getting attacks would be expected.
But there are certain measures and preparedness you can take from your side, to minimize or reduce all the risks of DDoS attacks. But before that, you might have been wondering what does DDoS attack means? What are the main objectives of such attacks and how come you get over these attacks in the future?
All these questions, we will be trying to cover and explain in this post in the most comprehensive way. So for that, you must keep reading this article till the end, get all your doubts clear in a single go.
Let’s get started!
What is A DDoS Attack?
A Distributed Denial of Service attack or DDoS attack is a hacking method used to incapacitate online services and websites. Attackers do this by flooding the service with an influx of bogus connections and data to overwhelm the servers and shut them down. These types of attacks have become very frequent in recent years with major online outages and the shutting down of popular websites and online services.
According to an ATLAS Threat report, over 2000 DDoS attacks per day are detected by Arbor Networks all over the globe.
How does DDoS Attack Work?
A DDoS attack is started by spreading malware through emails, USB devices, website downloads, or other mediums. This malware is automatically installed onto devices and keeps running in the background, spreading itself further and creating a large network of infected devices. This network can reach up to millions of devices. Once they have enough devices in their network, the attackers will be able to control them remotely and use these devices to attack their target by overloading their servers.
While not everyone has the necessary skills to carry out a DDoS attack, there are places on the dark web where week-long DDoS attacks can be purchased for as little as $150. This adds to the utmost need for protection against such attacks. Knowing what you’re dealing with is the first step.
There are some terms associated with DDoS attacks that you must know to clear all your confusion and helps you to better understand the concept of DDoS attacks.
What is the difference between DDoS and DoS attacks?
Many of you often get confused between DDoS and DoS attacks. But to understand how DDoS attacks work it is also important for anyone to get things clear and the terms related to them.
To understand simply, a DDoS attack is a subcategory of a DoS attack. Where DoS attack uses a single internet connection to overburden a target with multiple fake requests and try to infiltrate cybersecurity to increase vulnerabilities.
Whereas, DDoS happens on a larger scale and uses millions of connected devices to attack their target. This huge volume of connected devices makes DDoS attacks much more difficult to tackle.
Understanding Botnets
Botnets are typically large networks of compromised computers that are primarily used to conduct DDoS attacks. Although attackers don’t necessarily need botnets to conduct DDoS attacks. Because attackers can also manipulate thousands of devices on the same network (Internet) that are misconfigured.
Attackers hack multiple computers or other devices and infected them with malicious codes, which work as a bot. When these infected computers are connected to the same network, it is known as botnets.
After that, now the attackers can easily command the botnets to overburden the target’s servers with millions of connection requests that it becomes impossible to handle.
If you like our article we are sure you will like our services. Get FREE Business Emails, SSD, SSL, themes & plugins, dev & server support, and lots of other features with all our plans starting at $16.61 per month.
Global DDoS Attack Data
As per Statista, the United States has been one of the major shareholdings of Global DDoS attacks with 35.3% in the year 2021. Where the United Kingdom was at the second position with 29.4% and China in the third position with 18%.
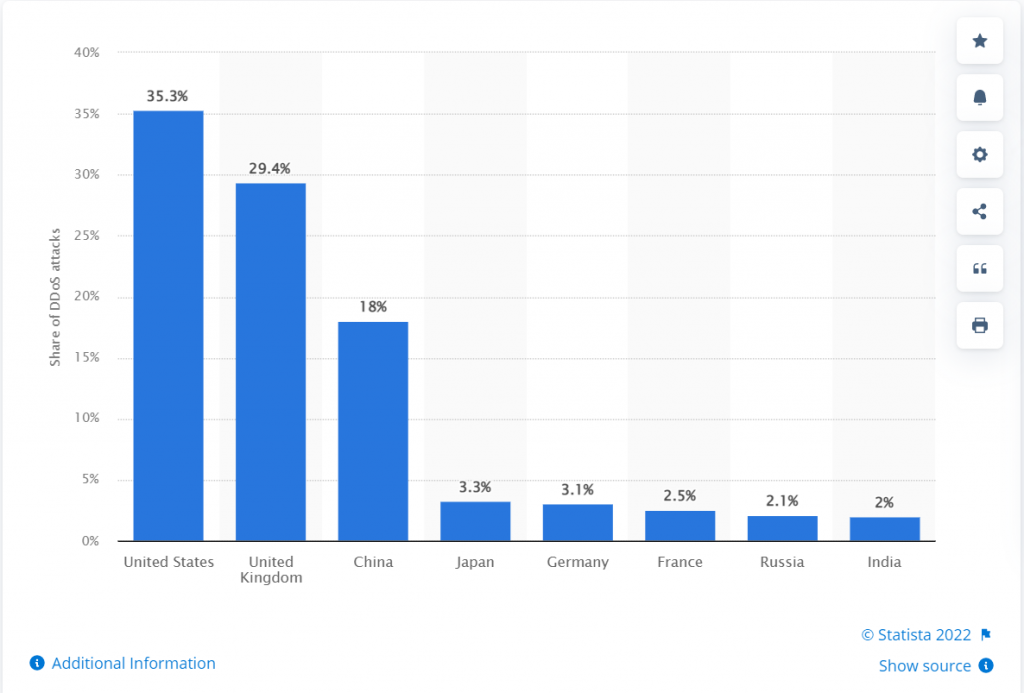
This shows the US is one of the most targeted countries for DDoS attacks. In which the computer and internet are the two most targeted industries.
And according to a leading website A10 networks, the majority of the attacks were launched from
- China
- The US
- Korea
- Russia
- India
In which China topped the list. Here you can check out a DDoS attack Map for your reference.
DDoS Attack Map
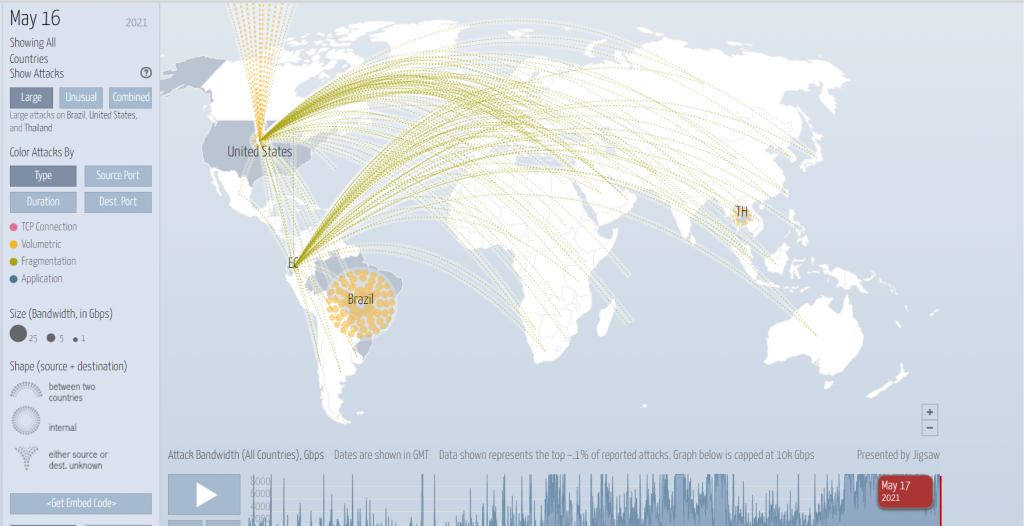
On 17th May 2021, the major attacked countries were Brazil, the United States, and Thailand.
How can You Detect A DDoS Attack?
These cyber security attacks often happen gradually without any signs or warning. And it can even be very difficult to anticipate or detect this until the network has been overloaded with inrush traffic and damages the system to the extent that it becomes nonfunctional.
But to detect these suspicious activities before they escalate quickly, the ISPs or Network Admins will inspect any suspicious traffic that emerges all of sudden from a single IP address or range.
On the other hand, if you were unable to prevent it on time, quick detection should be your topmost priority that helps to stop further damage.
Hence, it becomes very important that you must monitor and make a complete defense strategy that helps you to become prepared for any mishaps in advance.
However, there are some signs and areas that you must look into and check whether your website has been DDoS attacked or not? Let us check them out what they are:
1. Abruptly Receiving Large Emails
When you notice a large number of emails flooding your email inbox, then it is a sign of a DDoS mail flood type attack. However, receiving a small amount of spam email is normal and you will receive it daily which you can ignore.
2. Lower Server Speed
As soon as the DDoS attacks are conducted, your website will face a drastic change in server speed and your website will respond in minutes rather than in seconds. But slow servers don’t need to be the only sign of DDoS attacks, there can be multiple reasons that affect the server speed.
But it is something that you must investigate and check out the root cause.
3. Your computer gets slowed down
Even DDoS attackers can target a specific machine such as your Personal computer and overburden its network, which causes slow down your computer performance.
If you find your device is getting slow or its performance has been drastically reducing, immediately contact your ISP or network admin and report the same.
This way, it will help you to check whether the performance has been compromised due to any maintenance or network issue. Where your network Admin will further investigate and check out the major root cause, it found DDoS attack, they can sort out the issue by diverting the traffic through a more secured route.
Why do Cybercriminals Conduct DDoS Attacks?
Since DDoS attacks are one of the most prevalent types of cyberattacks, that has been growing rapidly in recent years. But to understand the major reasons behind all these attacks, first, we need to understand the main motive or objective of the attackers behind all these.
So here we have gathered some of the major points that attackers are primarily motivated by:
1. Mismatch Ideologies
Sometimes, if the ideology of an attacker doesn’t match with the websites or the content that they publish. They try to show their protest by attacking these websites with DDoS attacks and calling themselves “hacktivists”. These attacks often happen to target oppressive governing bodies or to show protest or support against some laws and interests.
2. Business Envies
Ideally, there should always be healthy competition between businesses. And they should try to outrank each other in SERPs organically. Such as, if your competitor is using some of the best SEO tactics, pushing high-quality content regularly, and increasing their conversion rate to outperform your website, all these methods are considered to be healthy and legitimate.
But due to envy, some Businesses follow the dirty or illegitimate paths to bring down their competitors. Such as hiring a hacker who will DDoS attack your website to damage your business and turn down your website.
For example, you are running a website xyz.com and your competitor has hired someone to DDoS attack on your website to bring you down.
When it takes time for your website to get back on track, the competitor will use this time to further damage your website by using bots that click on the ads that you were running and consume your daily marketing budget. In addition to that, they can also run spammy ads using your Brand or business name as a keyword and malign your brand reputation.
And eventually, you will lose your SERP rankings and you will notice your competitor is now ranking in the top positions.
3. For Extortion
Some of the DDoS attacks are conducted to get monetary gain from Extortion. For example, Cybercriminals often use a combination of DDoS attacks with ransomware that hostages the vital data of any organization from the website and locked out the owner until a ransom is paid.
4. Cyberwar
During warfare between two countries, the digital battle has also become prevalent. In which, the actions conducted by one country to attack and damage another country’s IT infrastructure or computer networks through DDoS attacks or computer viruses.
What are the reasons that make your website vulnerable to DDoS attacks?
Some sites make them much more vulnerable to DDoS attacks than others. Each website follows its preparedness and methodology to tackle these attacks. Which gives them an edge over each other in terms of cyberattacks.
But no matter how advanced methods or tactics you follow to tackle these DDoS attacks, there are some basic points you must follow to minimize the risk at the very ground level. Let us see what they are:
1. Unreliable and cheap Hosting
One of the major reasons that are responsible for DDoS attacks is the selection of unreliable and cheap hosting services. No doubt these cheap hosting providers deliver your services at very cheaper rates and yet generate revenues. But you might have not noticed that to make it affordable the hosting provider allows a large number of clients to use the same server.
This means, if any of the websites get attacked, it will also affect other websites that are on the same server. In addition to it, for cost-cutting, the cheap hosting companies will also not provide DDoS protection, warn you about the risks, and even won’t help you to repair your website if it’s not functioning.
They won’t provide daily backup and monitoring of your website. If they do, you have to figure out the whole process by yourself.
But if you are running an online business or personal blog, where your reputation and its security are your utmost priority, then it would be worth paying extra for reliable and best web hosting.
Spending on the best web hosting services would be worth every penny when you do not have to spend a lot of time to get your website back after being attacked which means your website will be online with up to zero downtime irrespective of any cyberattacks.
WPOven offers a completely secure and safe environment for WordPress websites to grow, without any tension or fear of Cyber or malware attacks. We offer you a 100% security guarantee against DDoS attacks and Firewalls protection.
2. Poor Preparation
If you have not followed any security measures and taken necessary actions to protect your website, then you are putting your website at risk. Since you can’t predict or anticipate DDoS attacks and even it is very tough to detect and prevent them.
In this case, you should be prepared enough and you do not have to suffer much if you have been attacked.
So, to avoid such a situation and minimize the risk and possible security damage, the first thing you need to do is to take all advanced and latest security measures. That helps to reduce the consequences of attacks and keep your website online.
Install some security software such as antiviruses and enable security alerts provided by your Hosting provider, that notify you when your website comes under attack, and necessary actions could be taken either by you or your hosting provider in time.
Enable automatic regular backup so that if anything went wrong with your website, you can easily restore and get it back like it was before.
3. Outdated software
Keeping Updated your WordPress software, plugins and themes won’t guarantee you complete protection from DDoS attacks. But in case your website has been attacked and your website weak spots have been used by the attackers to gain access to your website data, it will be less possible for them to get success if your website is well configured and updated.
It is always said, “Prevention is better than cure”, so on this principle, you should keep your website up to date and use only those plugins or themes that are from reliable sources as well as necessary.
Be careful and avoid installing plugins of themes from third-party sources even if it is provided free.
Types of DDoS attacks
There are three common methods used by attackers to carry out a DDoS attack. These include:
1. Volumetric Attacks
These types of attacks attempt to consume the bandwidth of the target by sending and receiving large data packets between the target and the network of infected devices. Even ‘unlimited’ bandwidth has a limit so this has caused many major online services to shut down their services or hastily add more expensive bandwidth to cope with the attacks. For example:
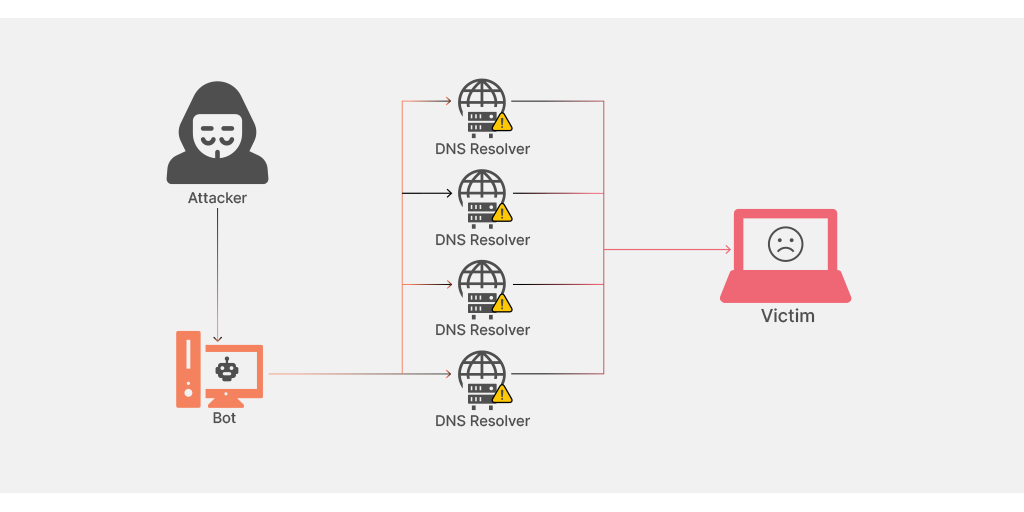
DNS amplification
In DNS amplification, the attacker exploits the vulnerability of open DNS servers to overwhelm a target system with DNS response traffic. The basic technique to conduct this type of attack is that the attacker sends a DNS lookup request to a publicly available DNS server having the victim’s address as a target.
2. Protocol Attacks
Fragmentation attacks work by sending out small packets of UDP or TCP data fragments to the target through the network of devices. The target becomes bogged down by the process of having to re-assemble the multiple data streams and this can lead to severe downtime. For example,
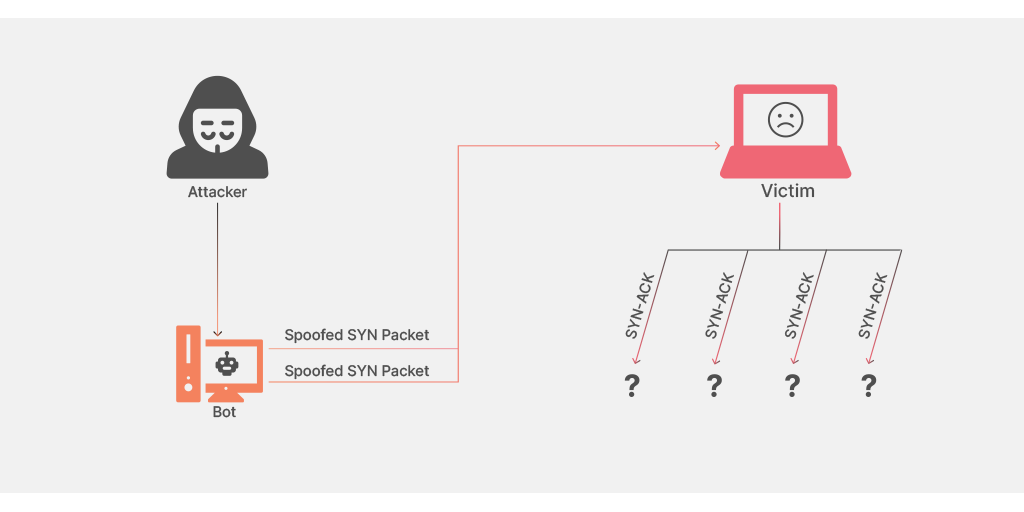
TCP connection attack (SYN flood)
Every device or server has a limit to the number of connections that can be made to it. A TCP connection attack focuses on overloading the number of connections to a server or device, leaving the service inaccessible as no more open connections are available. This type of attack sends one connection from each device on its network and can be very large scale, even shutting down servers that are prepped for millions of connections.
3. Application Layer Attack
These attacks target a specific application or part of the target service. Due to their specific nature, they can be carried out with a smaller network of infected devices and are harder to sniff out. For example,
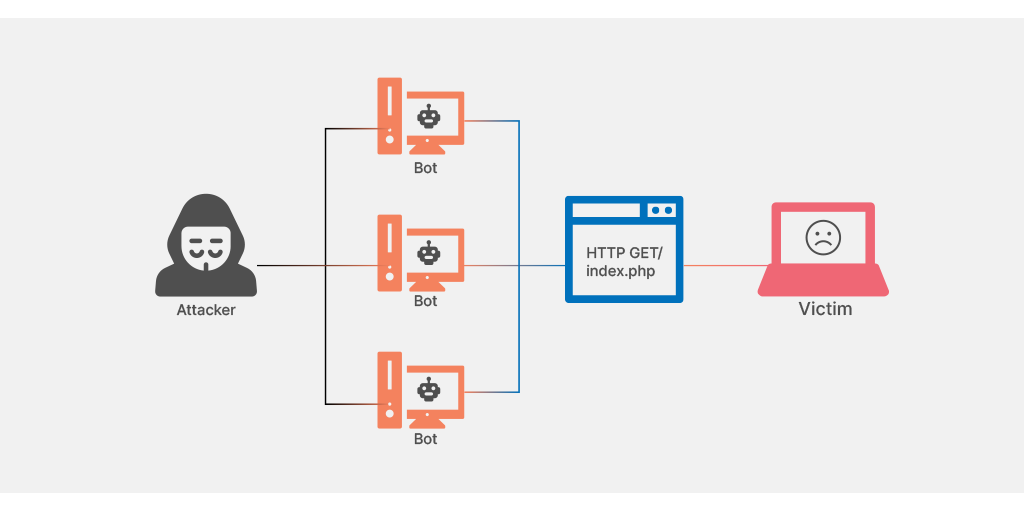
HTML Flood
When a large number of HTTP requests overwhelm the server at the time, it turns out to be a DDoS attack. The attack is quite similar to a large number of users pressing the reload button again and again on their browser for the same website simultaneously.
Some DDoS Attack tools that Cybercriminals use
There are several DDoS attacks tools available with the help of which cybercriminals target organizations. So, we are listing some of the widely used DDoS attack tools so that you can easily acknowledge them.
- Botnets: A network of compromised computers are used to conduct DDoS attacks.
- LOIC: A Low orbit Ion cannon is an open-source testing tool with the help of which TCP, UDP and HTTP server, the attack is being carried out.
- HOIC: High orbit Ion cannon is a modified version of LOIC, by increasing its capabilities and making some changes to it. And it is used to conduct large scale volume-based attacks in less time.
- R.U.D.Y: A RUDY or R-U-Dead-Yet is a low and slow DDoS attack tool that uses long form field submission using Post method.
- SLOWRIS: Considered as one of the best tools for executing DDoS attacks. It sends authorized Http traffic without affecting other services and port on the target network. It tries to keep maximum connection engaged and overburden the server as long as they are needed. Hence, there is limited or no space left for the users to attend.
- Tor’s Hammer: This tool is used for attacking Apache and IIS servers with an advantage of the tor network. Hence this tool is best known for its anonymous attacks and use this feature to evade firewalls and security layers.
- Pyloris: This tool is famous for executing stealth DDoS attacks and it is found to be very effective.
What to do if you’re attacked with Denial of Service Attack (DDoS Attack)?
1. Identify the attack
The first step is to know about the attack. Due to their nature, DDoS attacks are normally not detected until something goes down and the attack is well underway. If you manage your servers, make sure you monitor the data regularly so you know what your regular data rates look like. You can keep an eye out for any spikes in traffic or connections from unknown or irrelevant IP addresses. Once you witness any of the symptoms, it’s time to go into damage control mode.
2. Defend your network
If you have access to your router, the first line of defense will be there. You can set a limit on the data rate of your router to prevent an overwhelming amount of data from reaching your servers. You can also add filters to your router so it rejects data packages from malicious IP addresses. You can also set it to time-out half-open connections more frequently and drop malformed or spoofed packages.
3. Call for Help
Once you’ve done all you can from your side, you should call up your hosting provider or ISP and inform them that you are under attack. If it is a large-scale attack, they will probably already be feeling the effects of it. They will also have the resources and hardware to deal with these attacks and letting them know would give you a much better chance of stopping the attack in its tracks.
There are also some applications and services that can be installed during an attack that helps to prevent the attack using various methods including black-holing, sink-holing, IPS-based prevention, and DDS-based defense.
How to Prevent a DDoS attack?

While damage control is necessary once you’re under attack, it’s a far better idea to be protected against the attacks in the first place. Here are some of the best ways to prevent DDoS attacks.
1. Web Hosting Protection
WPOven offers you a wide range of security features that help to minimize any risks or vulnerabilities of being a victim of DDoS attacks.
As a Cloudflare Certified Partner, we’re providing all of our valued customers with hardened security and protection, that has inbuilt features a secure Firewall, and DDoS protection. On top of that, we also provide a built-in Web application firewall, Bot Protection, and strict software-based restrictions that help in your website protection to the next level.
Another WPOven‘s best feature is that it strengthens website security by conducting Daily antivirus and malware scanning. So, you are not taken by surprise. In addition to it, we offer dedicated anti-Hacking Support, where our experts will help you to get your website back to normal in case of any serious DDoS or malware attacks.
However, it is also to be acknowledged that, no matter how strong and good your web hosting provider is. No one can provide a 100% guarantee of protection against DDoS attacks. But a Good hosting provider can provide you with top-level security and a good firewall system that helps minimize the risk and damage to your website.
2. Intelligent Hardware
Used along with switches and routers, Application front-end hardware is placed before the data stream enters the network. These intelligent devices can detect any abnormalities and symptoms of a DDoS attack as soon as they enter the system by analyzing each data packet before sending it through. Most routers and switches can also be set up to detect a DDoS attack and can also be set to limit the number of connections if needed.
3. Install Firewalls
A firewall can block access to the network based on the attacker’s port, IP address, or protocols. This comes in handy when trying to block repeat attackers.
4. Content Delivery Networks (CDN)
A web-based content delivery networks such as Cloudflare use an upstream filtering system that passes all the data through a ‘cleaning center’ using tunnels, direct circuits, or proxies. This filters out the bad traffic and sends good traffic to the service. Many CDN services provide round-the-clock protection against DDoS attacks while giving you a faster content delivery system.
Summary
DDoS attacks are one of the most prevalent types of cyberattacks that have become very common. It has the potential to threaten organizations and cause even heavy financial loss.
It is even impossible to provide complete protection against DDoS attacks. Since you do not have much control over your web traffic. However, you can prepare properly and follow the best strategies to mitigate the attacks and damage associated with them.
You can choose the best WordPress hosting that provides advanced and best protection layers and also implement some of the best security practices that prepare your website for any DDoS attack possible.
If you would like to add more points or have any questions regarding DDoS attacks, feel free to ask in the comments section below:
Frequently Asked Questions
What does a DDoS attack do?
In a DDoS or Distributed denial of service attack, multiple compromised computers are being used to attack the target and overburden the server which causes a denial of service for users to use resources.
Is DDoS attacking illegal?
Yes, DDoS attacks are considered illegal acts. As per the USA’s Federal Computer Fraud and Abuse Act. Any convict of a DDoS attack will have up to 10 years in prison and up to a $500,000 fine.
What are the 3 types of DDoS attacks?
The three major types of DDoS attacks are:
1. Volumetric Based Attacks
2. Protocol Attacks
3. Application layer Attack

I am a Co-Founder at WPOven INC currently living in Vancouver, Canada. My interests range from Web Development to Product development and Client projects. I am also interested in web development, WordPress, and entrepreneurship.






![How to Block IP Address in WordPress? Best Solutions [2023] Block IP Address](https://www.wpoven.com/blog/wp-content/uploads/2022/06/How-to-Block-IP-Address-in-WordPress-Best-Solutions.png)